Information Management
Information management (IM) helps teams access and manage information over its lifecycle, ensuring that the information is relevant, complete, verified, protected, distributed and managed. Simply put, IM is about maintaining a clear, accurate, and accessible picture of information to one or more audiences.
As stated in ISO/IEC/IEEE 15288 (6.3.6.1): ’The purpose of the Information Management process is to generate, obtain, confirm, transform, retain, retrieve, disseminate, and dispose of information to designated stakeholders’.
Fundamental Concepts
The INCOSE SE Handbook describes IM as the process that “plans, executes, and controls the provision of information to designated stakeholders that is unambiguous, complete, verifiable, consistent, traceable, and presentable”.
The IM process ensures that necessary information is created, stored, retained, protected, managed, and made easily available to those with a need and who are permitted access. It also ensures that information is disposed of when it is no longer relevant.
The scope of information to be considered is wide, addressing technical, project, organizational, integration, contractual, agreement and user information, and any other information deemed relevant for the organization, all of these designated as ‘information assets’ in this article.
Effective IM enables business objectives, as illustrated in Table 1 below:
| Objective | How is IM enabling the objective |
|---|---|
| Operational efficiency | Through organizing secured processes for the collection, access and distribution of the information |
| Support analytics and decision-making | Through managing, in a controlled way, the tangible and intangible information assets and preserving them against uncontrolled modifications, threats and loss (cybersecurity dispositions against digital threats, resilient storage structures and pre-defined disaster recovery dispositions) |
| Quality and security | Through managing, in a controlled way, the tangible and intangible information assets and preserving them against uncontrolled modifications, threats and loss (cybersecurity dispositions against digital threats, resilient storage structures and pre-defined disaster recovery dispositions) |
| Competitiveness and innovation | Through providing access to the crucial information needed to make decisions and through the capability to extract meaningful insights from information analysis |
| Compliance | Through planning the adequate dispositions and access controls to comply with legal requirements, intellectual property and regulations applicable to information and data |
From a business enterprise perspective, the systems engineer, as well as many other stakeholders involved in systems development, may be involved in several activities that support the management of information across the enterprise and its projects. It may include strategic planning, analyses of technology/business trends, development of applications, understanding operational disciplines, analytics supporting decision-making, resource control techniques, and assessment of organization structures.
Information Versus Data
Terms like artifact, asset, work product, and documentation are commonly encountered in system engineering projects and are often used interchangeably to refer to information and data without regard to their difference.
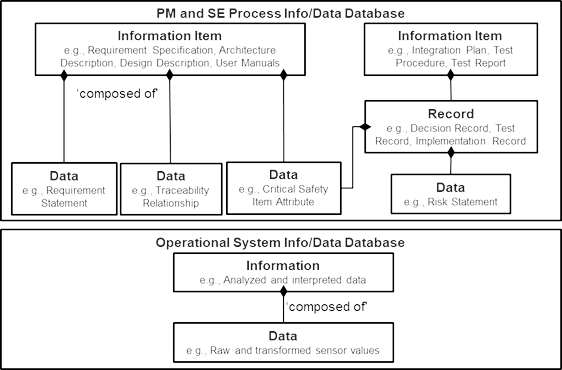
ISO/IEC/IEEE 15289 describes data as outputs of life cycle processes that can be individually recorded and managed, composable into a structure set and treated as a unit called a record, and part of information items (documentation). Information items (documentation) “are produced and communicated for human use and contain formal elements (such as purpose, scope, and summary), intended to make them usable by their intended audience”.
ISO/IEC/IEEE 15289 also describes the content for the general and specific information items that are inputs and outputs from life cycle processes. (Remark: U.S. DoD projects use MIL-STD-963C to describe the contents of information items).
Similarly, GEIA- STD-927B defines data as “A representation of facts, concepts, or instructions in a formalized manner suitable for communication, interpretation, or processing by humans or by automatic means” and information as “Data organized in a form that can be interpreted by humans or computers. Note: these definitions are “frequently used to discriminate between uninterpreted measurements (data) and meanings derived from raw data through some form of analysis (information)”.
Data Management Body of Knowledge (DMBOK) acknowledges that data and information can be differentiated in a similar way if it will better enable communication within an organization. An example of these relationships is shown in Figure 1. Conversely, GEIA-STD-859B defines data as “information that has been recorded in a form or format convenient to move or process”.
Figure 1 below shows examples of relationships between data and information items in a project. However, it should be noted that this figure only mentions a few examples of data and information items that may have a much broader scope in a project or organization.
Using the above-mentioned standards, we can synthesize a convenient definition for information and data: data are raw unstructured values, and information is structured data in context that has been analyzed and interpreted.
Even though information and data are different, some organizations may choose not to differentiate between management of the two. The definitions, relationships, use, and management of PM, SE or Operational System information and data should be described in the project’s management plans or system’s configuration information, respectively.
Information Asset
An information asset is any piece or collection of information that must be managed independently.
The information items described by ISO/IEC/IEEE 15289 would be considered as information assets.
Information assets:
- can exist in many tangible or intangible forms in an organization,
- are either related to a specific system development project or held at enterprise level and made available to projects as required: e.g., Product Line Engineering information, generic procedures and processes,
- may be held in electronic format and/or in physical form: electronic or paper drawings or documentation, microfiche, photographic record, file, database…
Table 2 gives some examples of criteria that may be considered when choosing between formats:
| Electronic Format | Physical Format | |
|---|---|---|
| Pros |
|
|
| Cons |
|
|
Metadata
Metadata can be thought of as ‘data about data.’ It consists of ’data’ that characterizes the information or data to be managed: for example, the title of the information, the author(s), the provenance, or the status of the information.
Metadata is particularly useful to organize the information database, to use the information and to search and navigate across the information database. It plays a key role in the organization of the governance of the information and data and contributes to quality and integrity objectives of the IM process.
Information Management versus Knowledge Management
According to SE HBK, Knowledge Management (KM) differs from Information Management (IM) as it is managed at Organization level and focused on providing the capability to re-apply existing knowledge.
However, KM is related to IM when it addresses explicit knowledge captured in information assets. Also, IM can be used to aid the objectives of KM by providing the means to manage the information regarding the knowledge assets.
Some examples of information assets, which may be considered as knowledge artifacts at the level of the organization, include:
- Technical content: leveraging and capitalizing on past engineering documentation, manufacturing processes, standard test procedures, design guides…
- Architectural and Design patterns
- Reusable content, i.e. product line information, generic analyses, previous documentation reusable pre-defined templates…
- Process information: process definition documentation, instructions, “How-to” guidance, validation information for analytical tools (e.g. aero-thermo-mechanical analysis tools).
How Does Information Management Relate to Configuration Management?
Information Management (IM) and Configuration Management (CM) are closely interconnected: whenever information assets correspond to identified Configuration Information related to systems or products under Configuration Management, those information assets should be subject to CM.
As noted in SEBoK Configuration Management article, ‘CM is concerned with the significance and applicability of information in relation to the specific system elements with which it is associated, referred to as configuration information’, while the IM process deals with the management of information itself over its own lifecycle: information generation, collection, validation, transformation, dissemination, and disposal.
The IM process is also complementary to CM to ensure the traceability of information in Configuration Management perspective.
Information Security Management
IM incorporates the fundamental need to manage the security of information assets.
Information security encompasses the mitigation of all kinds of breaches (digital and physical ones) that may expose personal, proprietary and industrial data, with associated consequences in terms of cost, image, and financial damages. It addresses a broader scope than cybersecurity, which focuses on electronic data, devices, and systems. It must consider all forms of storage, including information on physical formats and even knowledge held in the minds of stakeholders.
It must address the protection of intellectual property and trade secrets and comply with legal and regulatory requirements protecting privacy.
A simple approach for information security, inspired from the detailed methodology available in National Institute of Standards Special Publication 800-160v1r1, Engineering Trustworthy Secure Systems, should plan the 5 major steps explained below:
1 - Define Sensitive Information:
Determine the levels of Information sensitivity relative to pre-defined criteria, according to the nature of information to be managed and to the regulations and norms to comply with
Examples: information aiming to identify an individual, health information, national security information, or competition sensitive information.
2 - Define Data and Asset Classifications:
Define a global classification dictionary with clear classification rules, in accordance with the levels of sensitivity and considering the whole set of stakeholders along the system lifecycle; these rules should consider the variability that may exist in case of large systems involving many organizations and countries.
3 - Determine Information Security Controls, that may include the following:
· Information encryption, for both use-cases of information at rest (stored or archived) and under distribution, with considering the induced cost, processing, network and coordination overhead
· Digital signatures Distribution restrictions in accordance with the classification, enforced either by procedures or tools, including non-disclosure agreements (NDAs) between organizations, making them liable in case of disclosure of protected information
· User security education with regular refresher training and monitoring
4 - Implement Information Security Controls:
Ensure controls adapted to each sensitivity classification and to the phasing of the connections across organizations (either existing or under development), with the adequate planned tools and resources
5 – Monitor execution:
Ensure measures to provide insights and status about information security, taking advantage of existing cybersecurity dispositions when available.
Information Management System
A dedicated Information Management system is needed to enable and support the IM process and its activities.
The IM system must comply with the involved organizations’ security policies along the full lifecycle of information assets.
A typical IMS includes capabilities to do or assist with the following functionalities:
- Collection and organization of data and information
- Storage and retrieval of both raw data and information
- Analysis of data to transform it into information
- Creation of relevant reports/reporting of the results per appropriate context for decisions
- Protection of data and information
- Management of the access rights, responsibilities and authorities over the information database
- Compliance with laws and regulations.
Engineering the Information Management System
The Information Management system (IMS) aims to ensure the functions identified in the previous section while guaranteeing information availability, reliability, provenance traceability, security.
The IMS stakeholders’ range may address a wide scope: project management, cybersecurity, systems engineering, specialty engineering disciplines, configuration management, quality management, industry, service functions, ... across one or several organizations.
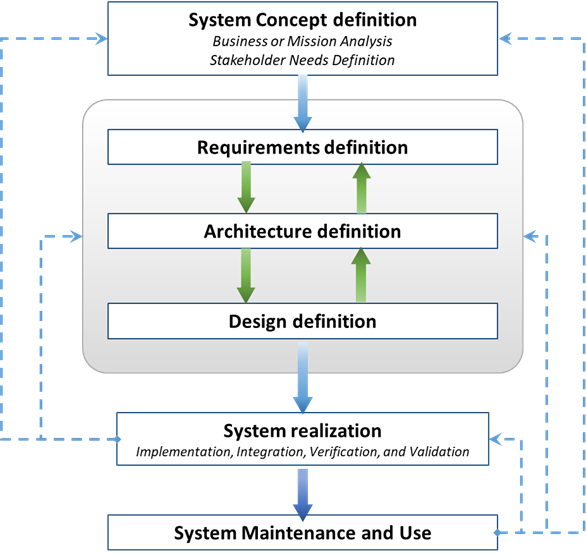
The life cycle processes can be used to engineer the IMS as the system in charge of answering to the organizational need to manage its information and data. An example of approach is shown in Figure 2:
Each major step in figure 2 includes several considerations of particular importance to IM:
- In Concept Definition (Business or Mission Analysis and Stakeholder Needs Definition):
- The involved stakeholders and organizations and their needs in terms of access controls
- The needs for security boundaries
- The needs for audits
- The applicable regulations, laws, protection requirements
- The information lifecycle requirements per type of information
- In Requirements Definition and System Architecture Definition:
- The existing structures and their constraints: repositories, cybersecurity architectures
- The existing information and configuration management processes (including problem reporting and change management),
- The existing syntax and semantics
- The disaster recovery dispositions
- In Design definition:
- Potential iterations when designing the IMS to consider changes to introduce new requirements for retrieval speed, archiving, metadata, data modelling, access rules
- In Realization (Implementation, Integration, Verification, and Validation):
- Incremental integration, verification, and validation of the IM system to enable a stepwise adoption of new processes
- Application of information and configuration management rules
- Involvement of stakeholders in tests to value their feedback
- Coordination with IT and cybersecurity staff especially during initial implementation steps
- In Maintenance and Utilization:
- Needs to adapt the information lifecycle, always controlled by dedicated processes (information and/or configuration management workflows)
- Regular disaster recovery and retrieval plan exercise
- Performance and quality monitoring of a dedicated set of indicators
- Stakeholders' feedback to maintain their involvement in the overall IMS quality.
Process Overview
The IM process relies on a defined approach that includes appropriate practices, methods, procedures, resources, and controls to establish and maintain a reliable source of Information.
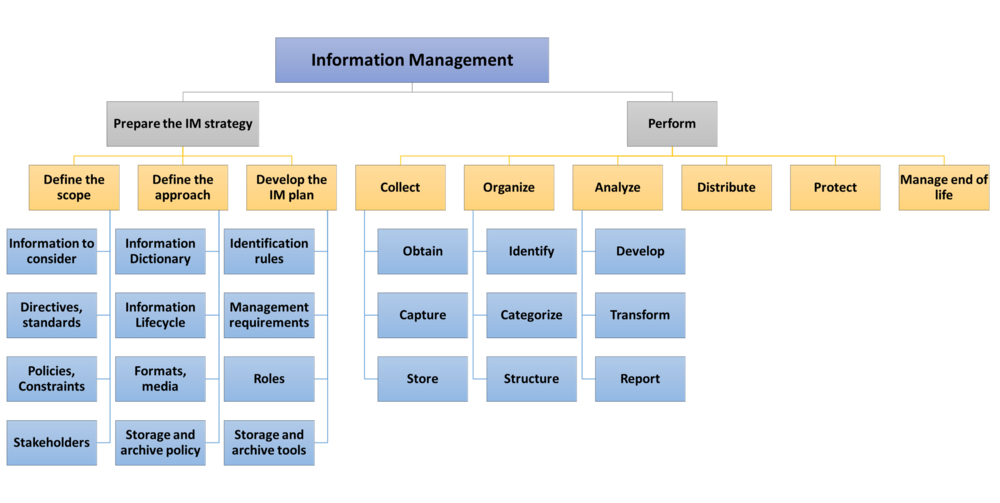
A decomposition is proposed below, inspired by the SE HBK IM section. Examples of decomposition could also be found in ISO/IEC/IEEE 15288 Clause 6.3.6, SAE 1001 Clause 5.2.5, ISO/IEC/IEEE 24748-7 Clause 6.3.6.
The benefits of the IM process are maximized when all activities are planned and executed. These activities are not sequential. They may be applied concurrently and iteratively as needed throughout the information life cycle.
Here are some insights about the proposed sub-activities:
- Prepare for information management (preparing the information management strategy):
- Define the scope:
- Relevant information and valid sources to be considered (business processes which will provide information)
- Directives, standards to be considered, including customers' requirements, industry standards…
- Policies, constraints: organization internal policy and directives, external constraints (e.g. legal, environmental, geographical, regulations)
- Stakeholders
- Define the approach:
- Information dictionary to consider the information to be managed (may be related to the project planning outputs in case of a system’s information)
- Information lifecycle:
- Stages and status of the information asset, from initialization until obsolescence and disposal
- Transition triggers between the lifecycle stages, defining workflows
- Change process to control the evolutions of the information, and when relevant, the traceable incorporation in Configuration Management baselines
- Authorized formats for capture, retention, transmission, retrieval, distribution
- Requests for adequate repositories and tools
- Storage and archive policy: retention duration, end of life disposal process, disaster recovery dispositions to prevent the loss of information in case of failure (back-up system, flawless recovery plan)
- Develop the IM plan:
- Identification rules: identification schema, mandatory attributes and metadata aiming to ease of search, rules for identifiers evolution
- Management requirements
- applicable to information capture, storage, validation, release, retrieval, and distribution
- problem reporting and change management, for both configuration information and information out of configuration scope
- control and security rules per type of Information, e.g. export control, access or distribution control, Intellectual Property, segregation of information between projects…
- auditing capabilities on the information database
- Roles
- Responsibilities: roles providing, managing, consuming, distributing information (including external distribution to suppliers, customers, partners)
- Authorities: roles in charge of IM policy and governance inside the organization, roles defining the IM system requirements…
- Storage and archive tools, consistent with the policy identified in the approach
- Define the scope:
- Perform information management
- Collect the information: obtain from the valid sources, capture and store according to the IM plan
- Organize the information: identify and categorize, structure the information to identify their relationships with the system’s elements to which they are related
- Analyze: develop or transform the information, report about the information to support decision-making
- Distribute the information to designated stakeholders inside the organization and to the relevant external stakeholders in accordance with predefined processes
- Protect the information: maintain integrity, security, privacy, in accordance with the applicable requirements
- Manage end-of-life: control information obsolescence, identify obsolete information and assess whether it should be archived or disposed of; it aims to prevent the uncontrolled growth of the information asset database by retaining content that should be archived or destroyed in accordance with applicable policies or agreements.
Elaboration
Information Management is involved in the management and control of artifacts produced and modified throughout the system life cycle and across the organization.
The list of types of information assets to be managed and their cadence in the systems engineering and project lifecycle should be defined in the planning process and documented in the IM plan. For information assets related to configuration management, their cadence should be consistent with CM requirements.
The IM process is therefore linked to configuration management, project planning, project assessment and control, system analysis, system detailed design definition, system realization, system deployment and use, system operation and service life management.
Practical Considerations
Key pitfalls and good practices related to IM are described in the next two sections.
Pitfalls
Some of the key pitfalls encountered in planning and performing IM are provided in Table 3:
| Pitfall Name | Pitfall Description |
|---|---|
| No Information / Data Dictionary | Not defining an information/data dictionary for the organization or for the project may result in inconsistencies in identification conventions for information, which reduces the accuracy and completeness of searches for information and adding search time performance. |
| No Information identification strategy | Not specifying the naming convention for information and identification rules may result in inconsistent information identification, difficulties to retrieve information and impossibility to ensure consistency of the information across the whole project or organization |
| No Metadata | Not defining the relevant metadata per type of information or tagging them inconsistently may result in ineffective searches based on metadata which are ineffective and can overlook key information. |
| No predefined Information / data lifecycle | Missing definition of the information lifecycle defining creation and validation workflow, release mechanism, obsolescence management, leading to uncontrolled creation and validation of information, overaccumulation of obsolete data |
| No security rules | Not defining the security classification levels nor the associated security protection mechanisms induce quickly high levels of risks of information leaks that could engage the legal responsibility of the organization |
| No clear information communication rules | Not defining the conditions for reception and distribution of information leads to lacks in traceability. Information should be considered as key assets and their communication across the stakeholders need to be organized |
| Missing content-obsolescence management | Not checking the currency and relevance of the information content, and not tagging obsolescent and obsolete information results in outdated information being retained and used inadequately, and induces an overload in the storage capacity needs |
| Missing access-obsolescence management | Not checking the currency and relevance of the access rights could lead to maintaining accesses to information that should no longer be proposed and lead to protection breaches |
| Missing information repositories-obsolescence management | Not considering the information management system applications maintenance and survey could lead to the loss of access to crucial information. The IM plan should include the management of the nominal repositories’ lifecycle, back-up solutions as well as a disaster recovery plan. |
| Inadequate back-up policy | Not ensuring that the information is backed up periodically in a back-up solution having the required retention durability and remains retrievable could lead to late discovery of information loss. The back-up policy should plan regular checks to ensure that information is not corrupted over time. |
Good Practices
Some good practices gathered from the references are provided in Table 4:
| Good Practice Name | Good Practice Description |
|---|---|
| Guidance |
|
| Information as an Asset | Recognize that information is a strategic asset for the organization and needs to be managed and protected. |
| Information Storage Capacity | Plan for the information storage capacity that is foreseen in your context, without forgetting to anticipate the increase of information volume based on the regular survey of the amount of information to be managed. |
| Effective Information Access | Ensure that the users are aware of the presence of the information and the relevant people access the information they need to know. Information that is not accessible or not used loses value that should come from the usage of the information. |
| Data Modeling |
|
| Quality Management | The cost impact of using poor quality information can be enormous. Be rigorous about managing the quality of information, including considering carefully the validation and release steps in the information lifecycle. |
| Information Repository Design |
|
| Uncontrolled modification prevention | Organize the information management life cycle and security to prevent from undesirable and/or untraced modification of the information. |
References
Works Cited
ISO/IEC/IEEE. 2023. Systems and Software Engineering - System Life Cycle Processes. Geneva, Switzerland: International Organisation for Standardisation/International Electrotechnical Commissions. ISO/IEC/IEEE 15288:2023.
INCOSE. 2023. Systems Engineering Handbook: A Guide for System Life Cycle Processes and Activities, 5th Edition. Ed(s): D. Walden, T.M. Shortell, G.J. Roedler, B.A. Delicado, O. Mornas, Y. Yew-Seng, D. Endler. San Diego, CA: International Council on Systems Engineering (INCOSE). Available at https://www.incose.org/publications/se-handbook-v5.
DAMA international. 2024, DAMA International’s Guide to the Data Management Body of Knowledge (DAMA-DMBOK2). Data Administration Management Association International. https://technicspub.com/dmbok2/
Ilana Hamilton. 2025, Article ‘Information Security Vs. Cybersecurity: What’s The Difference?’. https://www.forbes.com/advisor/education/it-and-tech/information-security-vs-cybersecurity/
Shirley M. Radack, National Institute of Standards and Technology. 2009, The System Development Life Cycle (SDLC). https://www.nist.gov/publications/system-development-life-cycle-sdlc
ISO/IEC/IEEE15289. 2019. Systems and software engineering - Content of life-cycle information items (documentation). International Organization for Standardisation / International Electrotechnical Commissions / Institute of Electrical and Electronics Engineers. ISO/IEC/IEEE15289:2019
ANSI/GEIA-859B. 2022. Data Management GEIA-859B. Arlington, VA, USA: Government Electronics & Information Technology Association. GEIA-859B Data Management
ANSI/GEIAHB859. 2006. Implementation Guide for Data Management GEIAHB859 - Arlington, VA, USA: Government Electronics & Information Technology Association. GEIAHB859
ANSI/GEIA-STD-927B. 2013. Common Data Schema for Complex Systems GEIA-STD-927B. Arlington, VA, USA: Government Electronics & Information Technology Association. GEIASTD927B
ANSI/GEIAHB927. 2007. Implementation Guide for Common Data Schema for Complex Systems. Arlington, VA, USA: Government Electronics & Information Technology Association. GEIAHB927
U.S. Department of Defense. 2019. MIL-STD-963C Data Item Descriptions (DIDs). https://quicksearch.dla.mil/qsDocDetails.aspx?ident_number=202450
NIST Special Publication (SP) 800-160v1r1. 2022. Engineering Trustworthy Secure Systems, by Ron Ross, Mark Winstead, and Michael McEvilley. https://doi.org/10.6028/NIST.SP.800-160v1r1
Primary References
ISO/IEC/IEEE. 2023. Systems and Software Engineering — System Life Cycle Processes. Geneva, Switzerland: International Organisation for Standardisation/International Electrotechnical Commissions. ISO/IEC/IEEE 15288:2023.
INCOSE. 2023. Systems Engineering Handbook: A Guide for System Life Cycle Processes and Activities 5th Edition. Ed(s): D. Walden, T.M. Shortell, G.J. Roedler, B.A. Del]icado, O. Mornas, Y. Yew-Seng, D. Endler. San Diego, CA: International Council on Systems Engineering (INCOSE). Available at https://www.incose.org/publications/se-handbook-v5.
ISO/IEC 27001. 2022. Information security, cybersecurity and privacy protection — Information security management systems — Requirements. International Organization for Standardisation / International Electrotechnical Commissions / Institute of Electrical and Electronics Engineers. https://www.iso.org/standard/27001
ISO/IEC/IEEE 15289. 2019. Systems and software engineering — Content of life-cycle information items (documentation). International Organization for Standardisation / International Electrotechnical Commissions / Institute of Electrical and Electronics Engineers. ISO/IEC/IEEE15289:2019
INCOSE. 2018. Integrated Data as a Foundation of SE. INCOSE Requirements working group. INCOSE-TP-2018-001-01.0.
ECSS-M-ST-40C Rev.1. 2009. Space project management — Configuration and information management. Noordwijk, The Netherlands: European Cooperation for Space Standardization (ECSS) - ECSS-M-ST-40C Rev.1
Additional References
None.